Redis cache, so fast, so easy to setup but a potential Chernobyl, lying within your system. The problem comes when the Redis cache is used as a permanent store of values within your system, so applications and services get to use it as stable source of truth. This is an easy trap to fall into […]
My Cloud Backup Approach
I have continously talked about my drive to never lose a file again, after I lost my first file to a failed floppy disk drive in 1996. The fanatical backup approach has been used to work as follows: Create a new version of whatever I am working on everyday – for files add the date, […]
Life and Tech – Choices, Decisions and Options
A couple of weeks ago Friday, I shared lessons from my life in technology with a team of upcoming software developers, Life in the Tech Lane, and I got a number of follow-up questions like the one below. On reading the questions, it spurred this post as the responses needed to be long form For […]
Voice of the ElePHPant Podcast – PHP, Technology Journey, Opensource, Java
I am excited to have been hosted on the Voices of the Elephant podcast by Cal Evans https://voicesoftheelephpant.com/2020/06/23/interview-with-stephen-s-musoke/ Talking about my technology journey, opensource, Java, PHP (of course) and what I am doing with it in Uganda and Africa
Perspective: User Requirements for Technology Projects
I was asked to talk about the handling of user requirements, how to link them to implementation within technology projects, by The Medical Concierge Group (TMCG) a digital ehealth service provider. The key principles are being able to respond to change (agile), keep learning, and how to capture business/customer outcomes as well as improving communication […]
Application and Data Security in the Software Development Lifecycle
This is presentation to Computer Engineering 4th year undergraduate students at Makerere University, Faculty of Technology, College of Design, Art and Technology to introduce them to concepts and approaches for application and data security in the software development process. [slideshare id=182745741&doc=muk-security-v1-191016095542] Looking for ideas on what I may have missed or omitted to help make […]
Life in the Tech Lane
I was recently asked to talk to a group of young technologists touching on career, health, finances and family. Using my own journey I am happy to share life in the Tech Lane [slideshare id=165517506&doc=techlife-v1-190822064953] I am happy to talk to your teams on similar topics, or even software delivery related topics, so do get […]
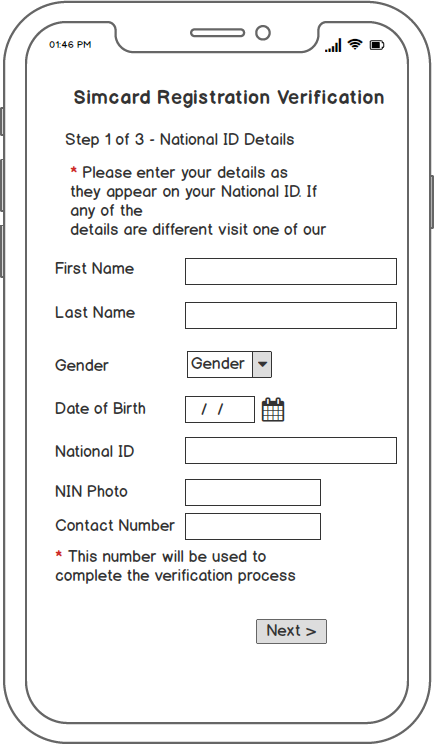
A Frugal Innovation Approach to Simcard Verification 2019 Edition – Design & High-level Architecture
Happy Easter Monday to you all, and I hope that the rains on Sunday night completed the cleansing process from the festivities, the resurrection of the Lord Jesus Christ and from the feast of the Goddess Ester (depending on which side you lean)… I am one who embraces all religious doctrines an faiths. So over […]
Social Expectations Perspective: Jumia – African Company or Not
This is the hottest topic right now with valid arguments on both sides of the equation, so here is my unsolicited opinion. What we can agree on is Jumia calling itself African is to look exotic, different to be able to raise its valuation hence more money to the shareholders. Arguments that this is a […]
Crowdsourcing Validation Rules for Uganda National ID
I am curious about the ability to validate that the Uganda National Identification Number (NIN) is well formed. However this does not validate that the NIN actually belongs to the person presenting it or that it is correct. The rules that I have been able to gleam are: Must be 14 characters long First character is […]